Log Insight Custom SSL Cert Upgrade Issue
Notes:
- If you are reading this after 4/30/23 and the SSL Certificates on your Log Insight deployment have expired – check out KB 92080. It contains the steps to replace the expired certificate in Log Insight.
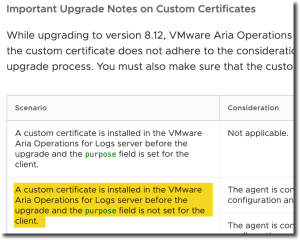
- As of 4/25 – the documentation in the release notes and KB articles have been updated to clarify steps to help identify custom SSL Certificates that may need to be recreated for Log Insight 8.12.
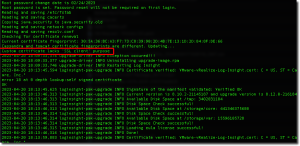
I ran into an issue applying the 8.12 version update to my Log Insight deployment. The upgrade failed fairly quickly and only sent a vague email that didn’t really provide any details.
The Log Insight upgrades I have done in the past have always gone smoothly and I haven’t had to really troubleshoot before, so I jumped onto the appliance via SSH to have a look. After I bit of poking around I found what I needed in the following file: /var/log/vmware/loginsight/upgrade.log
It contained an entry right before the errors:
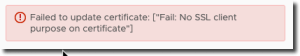
Custom Certificate lacks “SSL client” purpose
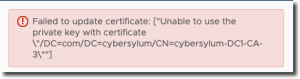
I had replaced the self-signed certificates with custom certificates generated from the Microsoft CA in my environment but thought I had followed the the steps in the Log Insight Documentation for SSL Certificates to generate the certificate properly.
I was in a bit of a rush to test the upgrade for someone (who didn’t use custom certificates), so I reset the custom certificates back to a default self-signed certificate in the Log Insight GUI (Settings -> SSL).
I retried the upgrade again and this time it worked! Log Insight was now upgraded to version 8.12 and had become VMware Aria Operations for Logs 8.12.
Out of curiosity, I tried to re-apply my custom certificate and received a similar error – No SSL Client purpose on certificate.
At this point I was determined to find the reason for this error, and resorted to reading the release notes. Low and behold – this is where I found a hint. Version 8.12 had some specific requirements for Custom Certificates.
Version 8.12 had come out to fix 2 critical issues (VMSA-2023-0007 & KB 91441). Due to the seriousness of the issues, I was upgrading within an hour of this version being made available to download so i could test.
In my hurry, I had skipped reading the release notes and re-learned a valuable lesson. Always read the release notes! I was able take the information in the release notes and combine that with some trial and error to figure out that some Extended Key Usage attributes should be added to the certificate.
Using Custom SSL Certificates with Aria Operations for Logs 8.12
You can use custom SSL Certificates with this new version of Log Insight. When creating the custom certificate you will need to enable 2 Extended Key Usage options:
- clientAuth
- serverAuth
I use OpenSSL to create the private key and CSR. You can follow those steps using the example config file below:
loginsight-openssl.cnf – note the extendedKeyUsage parameters in [req_ext]
[req] distinguished_name = req_distinguished_name req_extensions = req_ext prompt = no [req_distinguished_name] C = US ST = Ohio L = Columbus O = Cybersylum OU = Cybersylum Labs CN = loginsight.cybersylum.com [req_ext] extendedKeyUsage = serverAuth,clientAuth subjectAltName = @alt_names [alt_names] IP.1 = 192.168.5.4 DNS.1 = loginsight.cybersylum.com DNS.2 = loginsight
I modified the certificate template on my Certificate Authority to add the new required Extended Key Usage parameters:
- Open the Certificate Template Properties
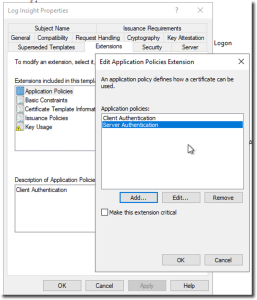
- click on the Extensions tab and select Application Policies. Click Edit
- Click Add and locate Client Authentication and Server Authentication
- Click OK and close the template
Using these steps, I was able to create a certificate from this template and add that to Log Insight Aria Operations for Logs 8.12.

6 thoughts on “Log Insight Custom SSL Cert Upgrade Issue”
Hi
Ran in to the same problem today did you find a solution ?
I was able to figure out steps that worked in my lab. I’ve updated the article – hope it helps!
Aaron.
In the exact same boat, “SSL client purpose”, thanks for posting this, looking for a workaround myself.
I was able to figure out steps that worked in my lab. I’ve updated the article – hope it helps!
After upgrade to this version active directory over ssl doesn’t work for me? Do you have the same issue?
I am afraid I have not seen that issue in my lab.