Using OpenSSL to create certificate signing request with Subject Alternative Names
Now that I had replaced the self-signed certificates in my vSphere environment, I started to wonder what other parts of my homelab could use the same treatment. While I worked on this, I learned how to use OpenSSL to generate a certificate signing request with Subject Alternative Names – and solved a problem. Read on for the details!
LIke most homelabs, I had a number of applications and devices
- vSphere
- VMware Skyline
- Realize Suite
- Synology NAS
- Ubiquiti Manager
- Webmin
The vSphere environment was already done. I was able to figure out the vRealize Suite fairly easily. Next up was one of the NAS devices I had, and this is where I ran into trouble. I was able to use the tools built into the Synology to generate a CSR and request a certificate from the Microsoft CA I had setup. The new certificate seemed to install fine; but the site was still showing as not trusted in my browser. I kept seeing the error : NET::ERR_CERT_COMMON_NAME_INVALID – even though the certificate was showing up as valid.
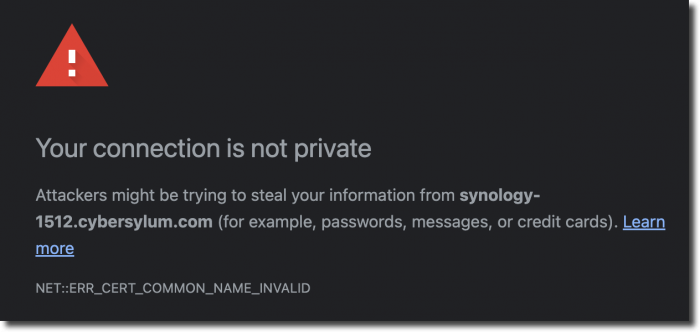
I reviewed the steps I had taken to create the certificate. Maybe i had not included the intermediate certificates correctly, so I re-worked that; but still ran into the same error. I was testing in alternate browsers and ran into an error message that helped give me an idea of what to try next: “the certificate does not specify Subject Alternative Names’
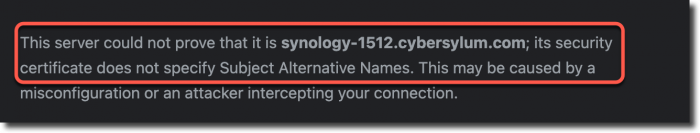
With this information, I revisited the Synology GUI; but there was no way to define any Subject Alternative Names (or SAN).
After a bit of research I found that OpenSSL can be used to generate the certificate signing request with Subject Alternative Names defined, as well as the private key.
Here are the OpenSSL commands that worked for me
Generate a private key
openssl genrsa -out synology-1520.key 2048
Create a configuration file that will be used to generate the CSR
synology-1512.cnf (create using the text editor of your choice)
[req] distinguished_name = req_distinguished_name req_extensions = req_ext prompt = no [req_distinguished_name] C = US ST = Ohio L = Columbus O = Cybersylum OU = Cybersylum Labs CN = synology-1512.cybersylum.com [req_ext] subjectAltName = @alt_names [alt_names] IP.1 = 192.168.4.3 DNS.1 = synology-1512.cybersylum.com DNS.2 = synology-1512
Create the CSR from the config
openssl req -new -key synology-1512.key -out synology-1512-openssl.csr -config synology-1512-openssl.cnf
Generating and testing the Certificate
I was able to take this CSR and generate a certificate from my Microsoft CA (using the Web Server template). It installed onto the Synology and to my great surprise it worked – the browser trusts the certificate and site!
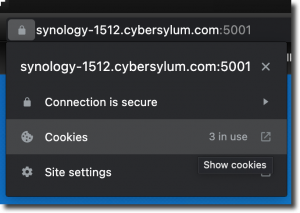
Not only were my browsers happy with this SAN-enabled certificate. I was also able to access the site securely with the IP Address, hostname, or FQDN.
Notes
- Keep those private keys safe!
- I kept a template config file for future use to save time
- If the device or application you are working with doesn’t provide a way for you to provide the key, end certificate, and intermediate certificate separately you can combine them in one file – just be sure to start with the end certificate and work through all of the intermediates.
This worked in my home lab. As with most things, there are probably other ways to accomplish the task at hand. I did learn a little bit more about SSL Certificates which is one of the best things about this hobby – Learn a bit more every day!

2 thoughts on “Using OpenSSL to create certificate signing request with Subject Alternative Names”
Thank you.
I’ve had other issues, and error reporting from the browsers have been limited.
following your guide an error came up – it’s fixed with adding -subj “/” to the end of the command
Thanks for reading and providing the helpful tip!